Black Friday is here and that’s why we wanted to bring you some information and cybersecurity facts because year after year, this day brings a peak in cyber attacks. Phishing, ransomware, data loss, and hacking are the order of the day, a trend that it’s most likely to continue rising. Just to give you an idea, ransomware assaults on Black Friday 2021 totaled 495 million worldwide.
With this in mind, every cybersecurity expert and common internet user might benefit from knowing the most common cybersecurity threats in this context.
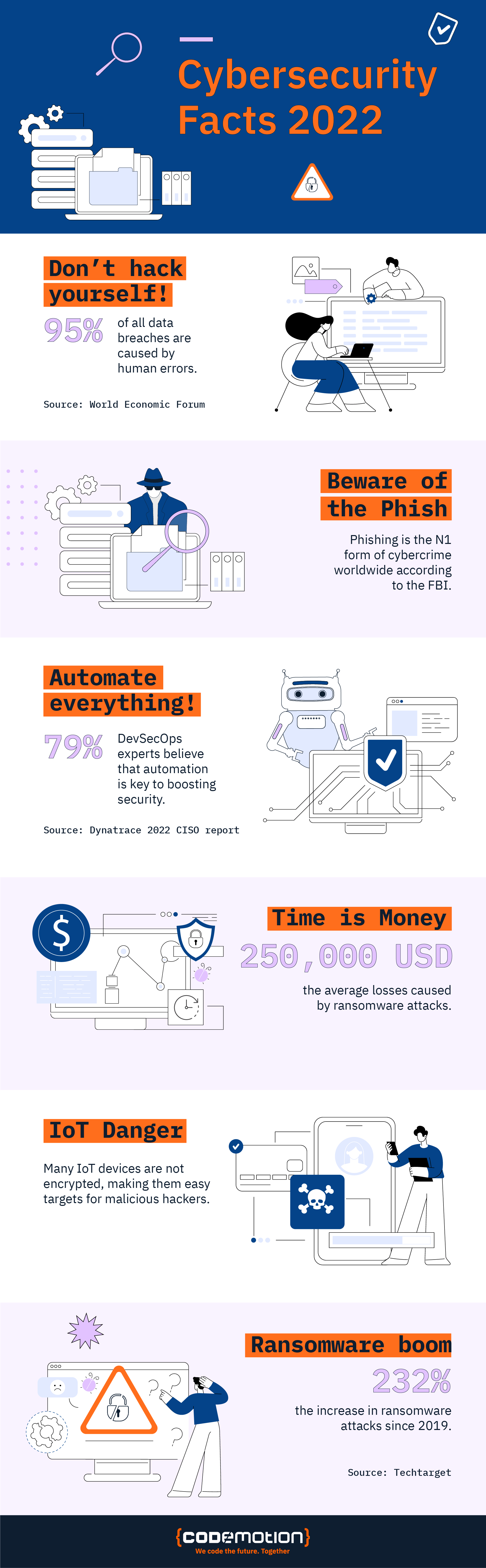
While firewalls and antivirus software are very useful, recent data shows that the main danger to data and sensitive information is users themselves. Yes: according to the World Economic Forum, around 95% of hacks begin “at home”, with users clicking on malicious emails, links, and downloading unsafe files: yes, even top hackers need you to help them to achieve their goals.
Take a look at the infographic we prepared to learn more about cybersecurity facts and trends:
Boosting security with automation
As stated above, most cybersecurity and DevSecOps experts believe that automation is one of the most powerful tools to combat the most common forms of cybercrime today. By using modern artificial intelligence and machine learning techniques, it’s possible for companies that handle sensitive data to generate higher levels of protection for their users and clients, and avoid potential breaches.
Automation with machine learning and AI is one of the cybersecurity trends that will undoubtedly continue to develop and in grow in the following years.
Playing the game against cybercrime
But why, even with these modern machine learning tools and processes at hand, is it so difficult to stop hackers and cyberattacks? Well, according to experts, the reason is that cybersecurity teams are always at a disadvantage against attackers: complex cloud and IoT systems today have many ‘entry points’ and vulnerabilities to cover.
In simple words, security teams have to work on many fronts simultaneously time every day, while hackers just have to find one small weak spot to achieve their goal and create great damage. That’s why cybersecurity teams are always training to be able to respond and solve eventual breaches (knowing that these will eventually happen).
One example of the exercises they make is the famous red-team vs. blue-team routine. This is an industry-standard by which developers can test the weaknesses of their systems internally, dividing themselves into two teams, one being the attacking team and the other one the defending team.




