Cloud service providers allow businesses to effortlessly host their data, without the need for technical hardware and with the promise of reducing costs. Sounds like a dream. But, cloud hosting also has the potential for cloud security mistakes. These mistakes can then lead to cloud data breaches. In fact, research showed that almost 80% of companies had experienced a cloud data breach since January 2019.
With the cloud services industry rapidly expanding to almost $200 billion, cloud security data breaches are also rapidly increasing. Research shows that in 2019 there was a 54% increase in the number of breaches from the previous year. This is why understanding and implementing cloud security is crucial for any successful business.
In this article, we have collected the five most common cloud security mistakes that businesses make and that you should avoid.
Cloud security mistake #1: Not patching your servers
One of the biggest cloud security mistakes a business can make is not being on top of their server patching management. Not only is this mistake especially detrimental, but it is also very common. A survey, that conducted research about company cloud environments, showed that 50% of the respondents were running a minimum of one outdated server.
The mistake businesses make is that they confuse general security updates with a company specific and effective patch process. Although cloud providers are responsible for providing businesses with some data protection, cloud patching, and application security should be maintained and regulated by the company.
Consider this scenario. You’re a company that provides channel routing software and you store a lot of sensitive customer information on the cloud. But, your cloud infrastructure doesn’t carry out patch management. This means that you are prone to a significantly larger percentage of attacks. In fact, data shows that 60% of breaches in 2019 were related to unpatched systems or servers.
With remote working becoming ever more popular, employees are now constantly using unsecured public networks. So, to reduce the risk of attacks and ensure company security it is vital that you carry out cloud patching. Here are a few tips you can use:
- Perform scans periodically. Carrying out regular scans will allow you to quickly identify any potential vulnerabilities and patch them accordingly
- Maintain visibility. A company that creates up-to-date records of all their devices and servers can easily assess potential vulnerabilities. This will also make reporting and assessment collection a faster process
- Don’t patch manually. Maintaining a server’s security is complicated. They often run varied operating systems and applications. These require different patches and this procedure would be too laborious to carry out manually. This is why it is essential to automate your patching process. Not only will this save you time but it will also reduce the amount of human error
Cloud security mistake #2: Not addressing zombie server risks
Zombie servers are servers that are not patched, validated, checked for vulnerabilities, or managed, but are still present on your cloud infrastructure. Data shows that there are more than 10 million of these servers across the world and they use up to eight power plants worth of energy to maintain. They are a financial burden, can be difficult to spot, and most importantly, they are a cloud security risk.
The main mistake businesses make is that they put off their zombie workload and do not act instantly to block them.
Zombie resources or comatose servers can actually prevent a company from detecting genuine cloud security risks such as cryptojackers. Not only that, zombie servers are a great indicator to potential attackers that you have weak security practices in place. This is because if you’re not detecting these servers, it is unlikely that you will be able to spot an attack. Attackers can also exploit the zombie servers to breach your security.
Here are the most effective techniques you can use to address your zombie server cloud risk:
- Maintain visibility of your entire cloud infrastructure. This should be a continuous process that provides you with full details of all the servers on your cloud. As mentioned above, zombie servers can be difficult to identify. So, instead of using a resource list, some companies use visual diagrams that allow them to view the full cloud layout and spot resources that have no connection to the others
- Label or tag any future resources. Creating a resource tagging protocol will allow you to keep tabs on all of your cloud resources. This makes managing useful resources and spotting comatose resources simple. But, it is vital that the labels you choose are easily understood by your employees
- After identifying, destroy. The most important part of addressing your zombie workload is actually terminating these resources. Using the best enterprise network security products is key as they can help in the identifying and destroying process and they ensure you determine the correct ones
- Create a zombie reporting culture. Companies that stay on top of their zombie workload prevent the risk of being overwhelmed. This is why making zombie resource identification and termination an aspect of your general reporting and auditing process is vital to maintaining a zombie-free cloud environment
Cloud security mistake #3: Not controlling your access
Access control is the concept of enabling specific users access to specific company data and information. But more importantly, it is also the method of preventing users access to restricted data. This is called access management. Efficient and secure access management requires both authentication and authorization of personnel. Take a look at this example.
Let’s say you’re working at a coffee shop and you’re analyzing private company information which you’ve accessed via an initial authentication process. The Wi-Fi is slow and the website loading time is taking a while, so you quickly go to the toilet. If your company doesn’t have a multi-factor authentication and authorization process then your data can be accessed by anyone whilst you’re gone. A multi-factor process can be anything from face recognition software to a key fob.
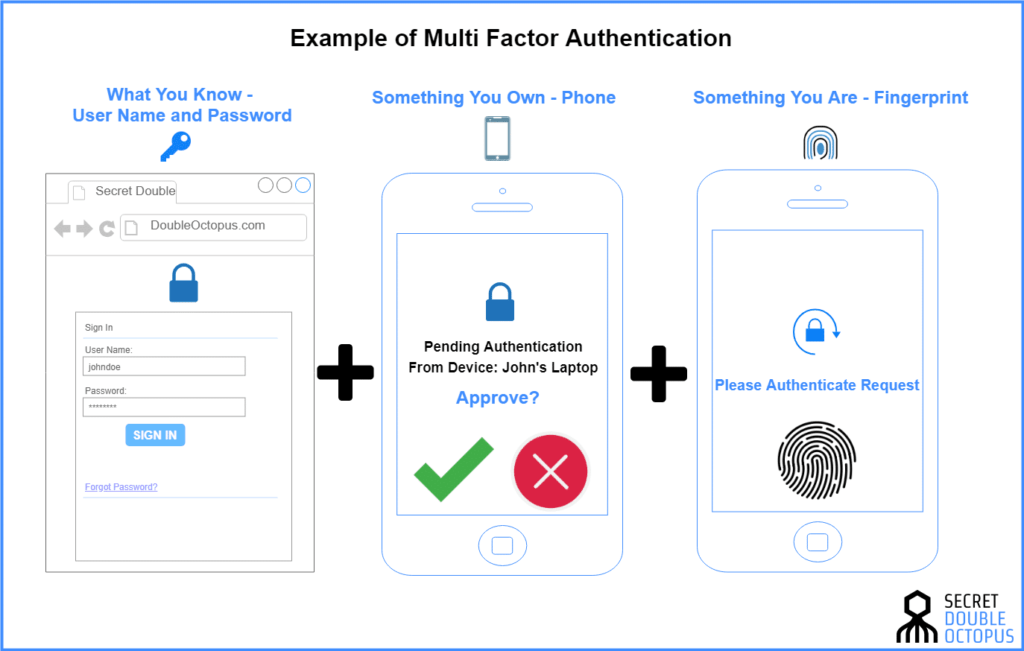
With remote working becoming ever more popular, this additional layer of protection is vital to ensure the necessary protection of your cloud information. Data shows that almost 70% of businesses don’t implement sufficient access management to control access to their cloud infrastructure.
Creating a good access management strategy requires you to understand the potential risks to your data and then implement a strict access control protocol. There are a variety of different access control techniques, but each business needs to adopt the appropriate method depending on how sensitive their specific data is.
Here are a couple of common access control models your business can take advantage of:
- Role-based access control (RBAC). This method ranks or separates employees to ensure that they can only access information or data that is related to their specific role. It is also the most common model used today
- Attribute-based access control (ABAC). This is a far more detailed and sophisticated method of access management. ABAC doesn’t only compare the employees’ roles, but every single attribute. This can include location, company position, specific time, and day of the week. This method is more appropriate for businesses that deal with highly sensitive information such as medical records
Cloud security mistake #4: Not creating standards for your encryption
Another crucial cloud security error businesses often make is failing to create a high standard encryption protocol. Many businesses rely on their cloud providers to encrypt their information, but data shows that less than 10% of all cloud providers encrypt data at rest.
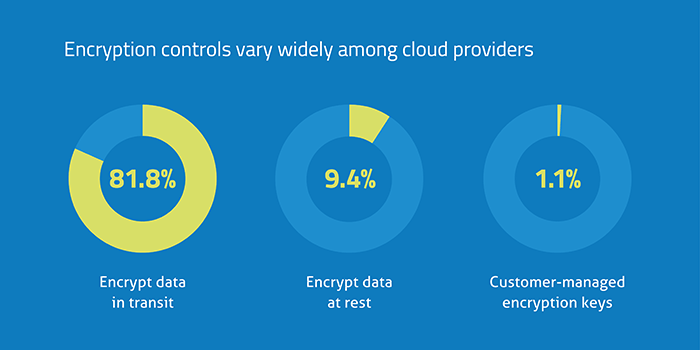
Data encryption is the process of transforming information before it is stored on cloud provider servers. For example, let’s say your company had a file named “Digital Customer Service Solutions: Choosing the Right Platform to Improve Customer Experience” which contained sensitive data. Using encryption algorithms, this information will be encoded into an unreadable format that cannot be deciphered by attackers.
Without encryption, this data has a greater chance of being breached by unauthorized users. Despite the amount of potential cloud security risk businesses can face, research shows that less than 30% of companies actually carry out full-disk high standard encryption.
Cloud encryption is especially beneficial if your company data is constantly transferred to different locations. Information transfer places data in a vulnerable state and opens up the possibility of unwanted surveillance or cyberattacks. But, encryption tools can provide your company with that security across multiple devices that prevents anyone but you from accessing or changing the data.
The next hurdle is then creating a cloud encryption protocol. Of course, every encryption policy or protocol will differ from business to business, but here are some points you can consider:
- Find out which specific data needs encrypting. Not every piece of information needs to be passed through the algorithm. You should assess whether the data falls under privacy acts or compliance requirements. Personal information and sensitive data to the company can also fall into this bracket
- At what point should the encryption begin? Company data records are dynamic, they are constantly increasing and updating. Data should be encrypted when at rest in the cloud. But, as mentioned above, data that is being transferred is vulnerable and should also be encrypted
- Decide who will manage the encryption keys. Encryption key management requires leadership because losing the keys can put the company at a detrimental risk. Cloud services can often provide their customers, aka you, with key storage and management. But, even if you decide to hand over the management to the cloud provider it is important that you implement access control. As we’ve mentioned above, this involves a multi-factor authentication and authorization process that ensures the security of your cloud information.
Cloud security mistake #5: Not deleting your data
Let’s imagine you’re a company that provides communication solutions for businesses, your customer’s experience shouldn’t just end with them purchasing the product. Providing reliable B2B customer service doesn’t only mean answering customer queries like “What is omnichannel routing and how does it work?”, it also means ensuring that private customer data is protected.
One of the biggest cloud security concerns is incomplete data deletion. This is especially problematic when companies change their cloud service providers or close certain accounts. Incomplete data deletion is not only problematic for your company’s data but it can also expose your customer’s private information.
Complete data deletion is a process that should be assisted by your cloud provider. But, it’s also your responsibility to ensure that the information has been removed in its entirety from the main servers, back-up servers, monitoring services, etc.
Here are a couple of steps you can take to ensure complete cloud data deletion:
- Remove information until it’s irrecoverable and inaccessible. This involves deleting information from every location and even temporary access points such as RAM and back-ups. This process should be carried out until neither the provider nor the customer can access the information
- Agree on deletion policies with your cloud provider. As a customer yourself, you need assurance from your provider that they will delete data within a given time period that you have predetermined and they should also provide you with proof of deletion. In the event of an error, your provider should carry out error handling to ensure that the mistake has been resolved
Cloud security is a vital part of modern business. It allows you to protect your company from any external or internal security threats and attacks. Without proper cloud security, you run the risk of losing control of valuable data and information and you increase the probability of a security breach. Data shows that the average cloud security breach can cost a company almost $4 million. This is why minimizing your cloud security mistakes is crucial to the success of your business.
Key takeaways
So, let’s quickly recap:
- Don’t just rely on your cloud provider to patch your servers, this should be a process you are constantly and automatically doing
- Zombie servers are costing you financially and are negatively impacting your cloud security by increasing the chance of attackers. So, don’t ignore the workload
- In the same way that you wouldn’t let anyone walk into your company office or warehouse don’t let them wander into your sensitive cloud data. Develop multi-factor access control for maximum protection
- Encryption is an efficient way for you to conceal data. Yet, many companies don’t do it. Creating your own encryption protocol is necessary for effective cloud security
- Incomplete data deletion has the potential to expose personal customer information and ruin your company’s reputation. This is why working with your provider and ensuring complete deletion is key