
A few weeks ago, I published an article mentioning cell-based architecture. I’d like to delve into the details of what this architecture entails and how it can be implemented with some additional information.
The Cell
Since primary school, children are taught that the cell is the smallest living organism. A cell is composed of various elements that allow it to perform basic functions such as feeding, breathing, storing resources…
A cell is built to be completely independent. It can cooperate with other cells to create larger organisms and is structured to maintain its characteristics intact and applies basic defense against external agents.
A cell performs basic functions; only the combination of different cells (and the consequent creation of complex organisms) allows for the implementation of more complex functions: a cell doesn’t have the ability to grasp an object, but the set of cells that form our hand make this function available to the human body.
The Monolith
Having dealt with various business realities, over the years I’ve faced the problem of monolithic applications: programs that were developed to give the end user an interface that directly connected them with the data they need to handle.
To begin dismantling monoliths, various patterns have been defined over the years, such as MVC (Model View Controller), which began to define 3 different components that can be developed independently and interact with each other through standard communication protocols.
This has allowed for increasingly detailed analysis and subdivision of the different components of each application, just as scientists have studied living beings and, through the use of appropriate scientific tools, have identified their basic components.
Starting from the Central Element
The definition of a capillary architecture to implement a business solution allows applying standard practices to each individual component in terms of:
- Scalability to extend the necessary resources to each single element
- Governance to constantly monitor the correct functioning of the single element
- Maintenance for each single element, a version is defined and the relative development and release process in dev, test, and production environments
Each cell does not define these components internally, but interacts with the organisms that implement them.
Cell Components
Each cell is a set of different components that are necessary to make it a unique and independent element. The elements within the cell can communicate directly with each other in a proprietary manner.
The cell exposes its services through standard protocols that are declared by documentation that supports common notions for defining interfaces.
External organisms to the cell do not know the internal elements and do not know which single component they interact with, but interface with the cell’s resources through a gateway that acts on the cell’s perimeter.
Antibiotics
Just as every cell in the human body can be attacked by a virus, this architectural component also needs to defend itself from pathogens. It is therefore necessary to define appropriate authorization and security criteria to defend the internal elements (applications and data).
Access through the APIs published on the gateway is therefore authorized by means of an Identity Provider (which can also be defined outside the cell itself) and the declaration of appropriate scopes for role distinction.
The domain of identities accessing from the outside may differ from that needed within the cell itself, where the access token to individual internal resources can be replaced.
Products
Below are some elements that can be used to compose individual cells and their purpose.
API Gateway
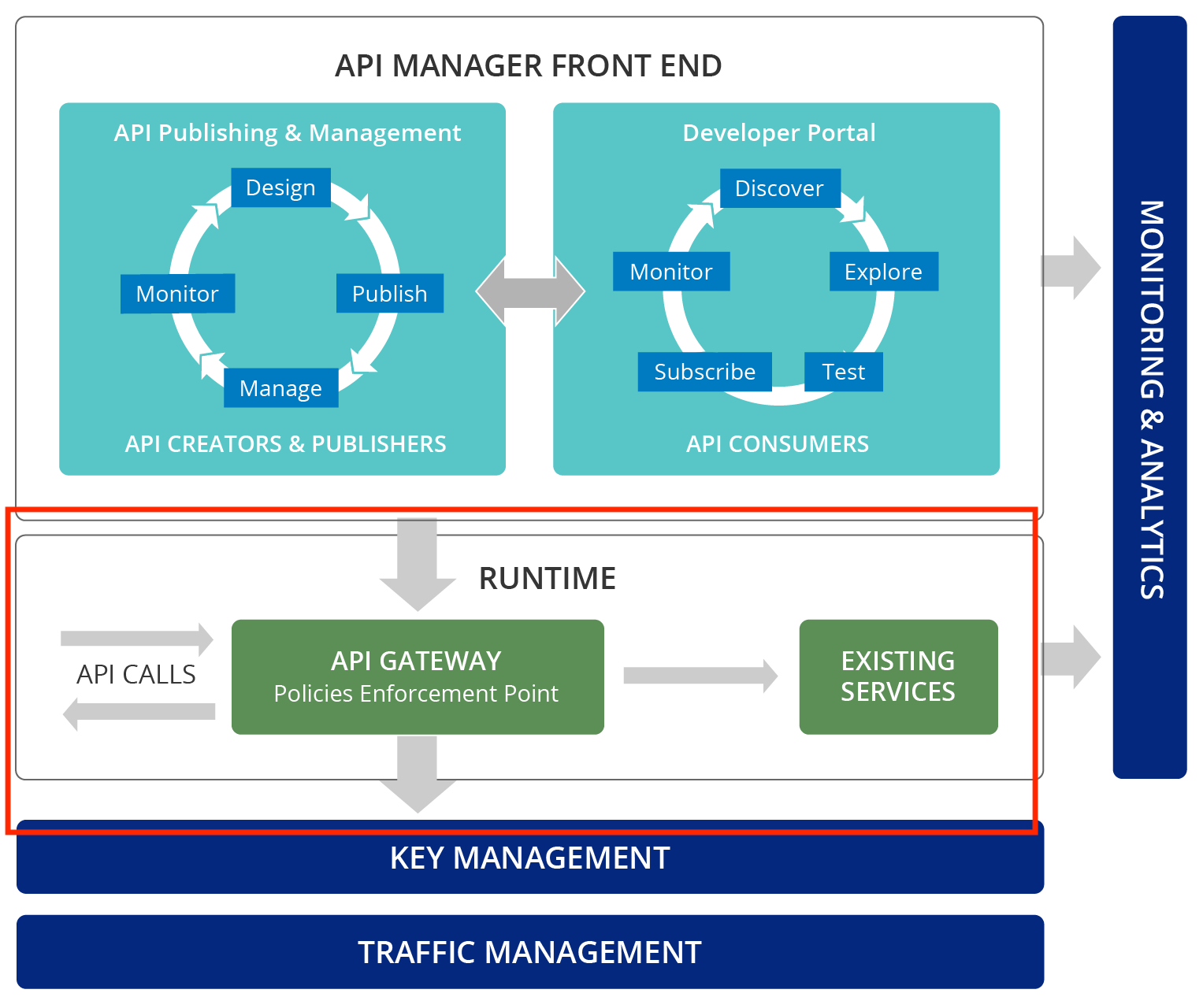
The API layer that the cell requires also needs governance for maintenance related to application evolutions and the drafting of related documentation to be published for external users.
WSO2 API Manager is the product for defining APIs, managing the lifecycle, and declaring security criteria on individual resources. The Micro Integrator profile allows implementing integration and transformation logics based on available microservices.
Security
From a security by design perspective, this topic needs to be approached from different points of view. Access to APIs can be validated through an Identity Provider; the integration of WSO2 Identity Server helps define authentication and authorization logics and integrates connectors for various external IdPs.
To go beyond perimeter security, one solution is to integrate 42Crunch, a product that scans the API definition to identify potential security flaws and provides a Firewall service that can be deployed in sidecar mode to validate APIs at runtime.
The 42Crunch platform automatically protects APIs from the top 10 OWASP security vulnerabilities. It can be natively integrated with development IDEs, CI/CD tools, and API runtime to have constant verification of potential security flaws.




